Recently a security researcher discovered a severe flaw in the Facebook Messenger and not only that this severe flaw could easily allow an attacker to read all your private chats.
This Simple Bug allows Hackers To Read All Your Private Facebook Chats
Until about a few months ago there was a serious vulnerability in Facebook Messenger, through which it was possible to infiltrate the conversations and change all the content without any user interaction.
The problem was discovered by the security firm, Check Point Software Technologies Ltd. which is an international provider of software and combined hardware and software products for IT security, including network security, endpoint security, data security and security management.
Now again a security researcher has discovered a severe flaw in the Facebook Messenger and not only that this severe flaw could easily allow an attacker to read all your private chats, simply affecting the privacy of around 1 billion Messenger users.
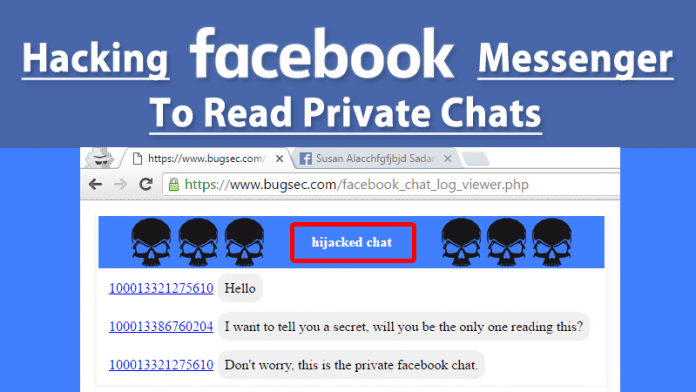
The security researcher of BugSec and Cynet, Ysrael Gurt, reported that the flaw which was discovered is a cross-origin bypass-attack simply towards the Facebook Messenger which allows the hacker to access all your private chats including the attachments as well.
Now, many of you might be thinking that how an attacker can use this severe flaw to hack someone’s Facebook Messenger?
First of all let me clear one thing the process is very easy, as to exploit this severe flaw, all a hacker or an attacker need is to trick the victim into visiting a malicious website and that’s it, as I told you all that the process is really simple.
However, this severe flaw is named as “Originull” and the issue was reported just after the discovery to Facebook team by the researcher of BugSec and Cynet, Ysrael Gurt. Once the victim clicked the link, all his/her private chats were get hacked whether he/she was in a Facebook’s mobile app or a web browser. Yes, this flaw affects both the web chat as well as the mobile application.
Here is what the security researcher of BugSec and Cynet, Ysrael Gurt explained “Communication between the JavaScript and the server is done by XML HTTP Request (XHR). In order to access the data that arrives from 5-edge-chat.facebook.com in JavaScript, Facebook must add the “Access-Control-Allow-Origin” header with the caller’s origin, and the “Access-Control-Allow-Credentials” header with “true” value, so that the data is accessible even when the cookies are sent”.
But, the social media giant Facebook Messenger’s end-to-end encrypted chat feature was not get affected by this severe vulnerability.
Moreover, the Chief Technology Officer of BugSec, Stas Volfus said that “This security flaw meant that the messages of 1-billion active monthly Messenger users were vulnerable to attackers”.
Later he also added that “This was an extremely serious issue, not only due to the high number of affected users, but also because even if the victim sent their messages using another computer or mobile, they were still completely vulnerable”.