Ransom32 is a new family of Ransomware discovered by researchers from the security firm Emsisoft. Billed as the first to use JavaScript as its source code, the ransom applicant was encoded via the NW.js framework, formerly known as Node-WebKit. NW.js allows developers to create Windows, Linux, and Mac OS X desktop applications using JavaScript.
It is based on Node.js and Chromium projects and uses a lightweight version of WebKit, the rendering engine used in Chrome, Safari, and Opera.
If browsers limit the interaction of JavaScript code with the underlying operating system, one of the peculiarities of the NW.js platform is that it removes those limits and thus gives developers much more control and interaction with the operating system.
If an application has NW.js need to be written once to be immediately usable on Windows, Linux, and Mac OS X. For now, only Windows PC appears to have been infected with Ransomware. As with many threats, Ransom32 is generally distributed via spam campaigns.
Ransom32 The First Ransomware JavaScript Able to Run on Windows, Linux, and Mac OS X
The malicious file is therefore attached to emails mentioning unpaid bills or notices of delivery, among others. The malware works as Ransomware as a Service (RAAS) and is distributed through intermediaries that subscribe to actors on a platform managed in the Tor network. This service allows any amateur to distribute the threat after setting up its customized version of Ransomware.
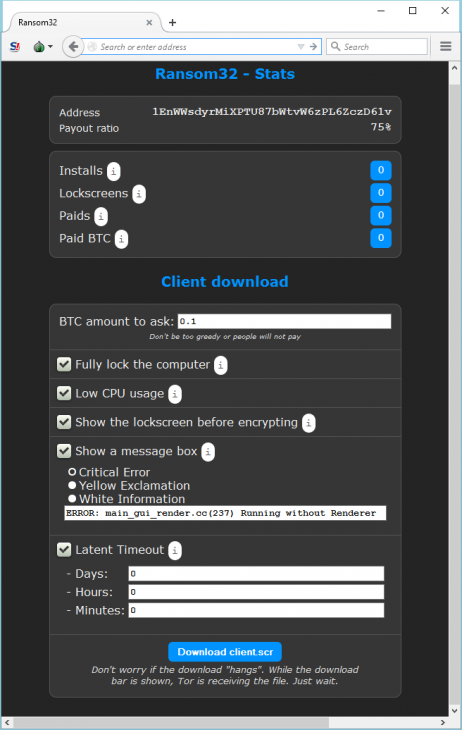
Everything you need to register and become a distributor is to provide a Bitcoin address on which the funds are generated to be paid. After each payment made by a victim, the funds are transferred to the account of the malware authors. Therefore, they recover a 25% commission before repaying the rest of the money to distributors.
At registration, future distributors’ ransomware access an administration page where they can perform some configurations. This page books various statistics, such as the number of people who have already paid or the number of systems that have been infected.
There, they can configure the malware (completely lock the computer, low CPU usage, etc.) but also set the number of bitcoins paid by the victim. Once this phase is completed, they can then upload their Ransomware which has a remarkable size of 22 MB
If, in general, the size of the malware does not exceed 1 MB, this unusual case here does not mean that this is the work of an amateur, says Fabian Wosar security firm. This rather commended the encryption used by Ransom32. It compares the original cryptolocker.
If Fabian could “break” ransomware many families in the past, he said this new variant is now indecipherable. Regarding the payload of Ransomware, it is a WinRAR self-extracting archive that contains all it takes to help the malware to compromise the computer of the user.
The archive contains a copy of the GPL license agreement, but a “chrome.exe” file is a packaged NW.js application. This application has malicious code, and the framework needed to run the malicious software.
This means that Ransom32 is not counting on any existing framework on the user’s computer. Among other files found in the archive is a small script that identifies and removes all files and folders in a given directory. WinRAR file also includes information about configuring the malware.
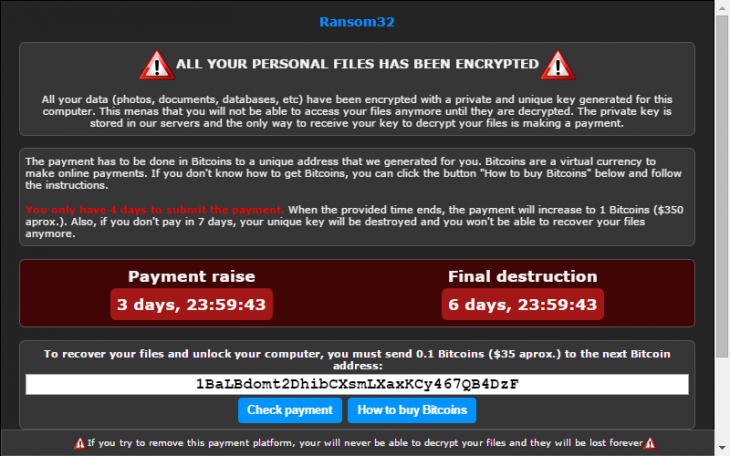
Once Ransom32 is executed, it extracts all the files in the temporary files folder and creates a shortcut in a user’s Startup folder to ensure the malware is run every time. It can then start to encrypt user files and ask the victim to pay a ransom at the risk of increasing or destroying the decryption key.