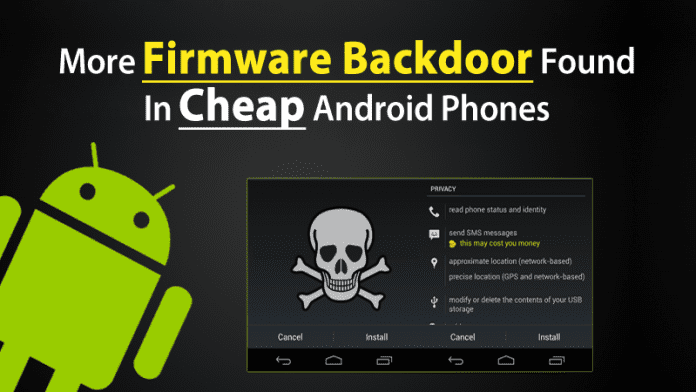
The security researchers at “Dr.Web” a Russian anti-malware company and the name of its flagship software suite have identified two critical pre-installed firmware backdoor in cheap Android smartphones.
Pre-Installed Firmware Backdoor Found In Cheap Android Smartphones
In many regions, the only way for manufacturers and sellers to reach consumers is through very inexpensive devices that sacrifice critics as the possibility of receiving frequent updates aspects, but that’s not all.
As those manufacturers also preinstall significant amount of unwanted applications which become very difficult for the users to remove all those unwanted applications.
However, with the advent and rise of Chinese mobiles, we were able to enjoy the appearance of a new range of devices ultracheap which often offer solvent properties, for almost ridiculous prices as we told earlier.
As it is evident, in most cases, these devices have some kind of cuts inside, they are simply just frustrating that the users’ always experience with most of the Chinese Android devices, transforming this into a critical vulnerability for the Android operating system, rather than to the manufacturer question, who really is to blame.
The security researchers at “Dr.Web” a Russian anti-malware company and the name of its flagship software suite have identified two types of downloader as Trojans that have been included in the firmware of a large number of popular Android devices running on the MediaTek chipset.
The trojans which were detected by the researchers at Dr.Web are “Android.DownLoader.473.origin and Android.Sprovider.7”, so, these two trojans can easily install digital trash in the background and even add advertisings as well. Apart from this, they are also capable of collecting crucial data about the infected devices, contacting their command-and-control servers, automatically updating themselves and even they can also run themselves each time when the device is restarted.
According to the Dr.Web “Another Trojan found on the devices Lenovo A319 and Lenovo A6000 was named Android.Sprovider.7. The Trojan is incorporated into the application Rambla which provides access to the Android software catalog named the same”.
“The payload of Android.Sprovider.7 is located in a separate program module (which is detected as Android.Sprovider.12.origin). It is encrypted and stored in resources of the main malware program. When a user unlocks the home screen, the Trojan checks whether the module is still active. If not, Android.Sprovider.7 retrieves this component from its body and runs it”.
“The module Android.Sprovider.12.origin can execute the following functions:-
# Download an APK file and try to install it by obtaining the confirmation from a user.
# Run an installed application.
# Open the specified link in a browser.
# Make a phone call on a certain number by using a standard system application.
# Run a standard system phone application in which a specified number is already dialed.
# Show advertisement on top of all applications.
# Display advertisements in the status bar.
# Create a shortcut on the home screen.
# Update a main malicious module.”
Here is the list of Android devices that are affected by the malicious firmware backdoor:-
# MegaFon Login 4 LTE
# Irbis TZ85
# Irbis TX97
# Irbis TZ43
# Bravis NB85
# Bravis NB105
# SUPRA M72KG
# SUPRA M729G
# SUPRA V2N10
# Pixus Touch 7.85 3G
# Itell K3300
# General Satellite GS700
# Digma Plane 9.7 3G
# Nomi C07000
# Prestigio MultiPad Wize 3021 3G
# Prestigio MultiPad PMT5001 3G
# Optima 10.1 3G TT1040MG
# Marshal ME-711
# 7 MID
# Explay Imperium 8
# Perfeo 9032_3G
# Ritmix RMD-1121
# Oysters T72HM 3G
# Irbis tz70
# Irbis tz56
# Jeka JK103
# Lenovo A319
# Lenovo A6000
So, if you have one of these devices, your data is at risk. However, the security researchers at “Dr.Web” have already informed smartphone manufacturers about this incident.