According to latest reports, recently, a completely unknown security firm raised the controversy by making public several bugs present in processors of AMD. However, now after that controversy, AMD itself has confirmed that its processors are vulnerable.
AMD On Chip Flaws: Newly Outed Bugs Are Real
A week ago CTS Labs, a completely unknown security firm, raised the controversy by making public several bugs present in processors of AMD.
Since then the industry has discussed at the time the consequences of this publication. The researchers notified the manufacturer just 24 hours in advance; In addition, the tone of the web they created and the publication of articles advising to sell shares of AMD made it suspect that, behind all this, there was an attack against AMD.
Are the AMD bugs real?
We do not know if the publication of these bugs was motivated by an attempt to harm AMD; but what was clear from the beginning is that the bugs are real.
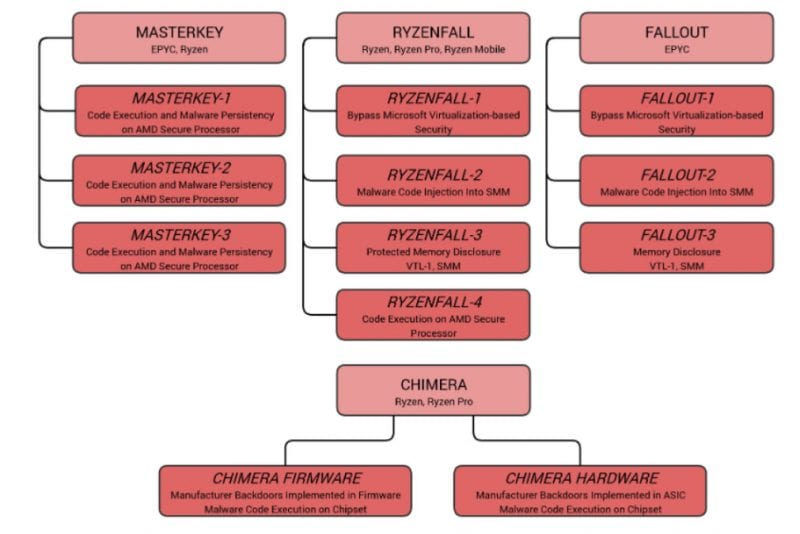
This has been confirmed today by AMD itself, which during these days has put its engineers to work at forced marches. The conclusion is that the vulnerabilities RyzenFall, MasterKey, Fallout and Chimera exist in Ryzen and Epyc processors, and can be exploited to attack our systems.
What parts of the processor are affected?
MasterKey, Fallout and Ryzenfall affect the Platform Security Processor, or PSP, a chip present inside the CPU, and which is independent of the AMD processor; is the equivalent to the Intel Management Engine present in Intel processors, and that also had its ration of problems. The PSP is dedicated to security, such as encryption keys or passwords.
Chimera, on the other hand, affects the AMD chipset, and therefore it is not a problem of the processor, but of the motherboard.
Is it really as serious as they paint it?
The reality is that these bugs are serious. but by themselves they are useless. All have one thing in common: to take advantage of them, administrative access to the system is needed; in some cases, you even need to be in front of the computer to take advantage of the exploits.
Therefore, we are not facing such serious bugs as Meltdown or Spectre, which did not need that kind of special access.
What does AMD plan to do?
Now that the impact of these bugs is clear, AMD has announced its action plan, in the form of patches that will be released in the coming weeks.
These patches will be firmware, so we will have to apply them at the BIOS level; It is still unclear if AMD will release these patches on its website or if it will be the manufacturers that will fulfil this function.
A very important detail and that also differentiates this problem from Meltdown and Spectre, is that these patches will not have an impact on the performance of the system.
Should I fear for the safety of my PC?
Probably not. For starters, if an attacker gets administrator access to your system, you already have another security hole, probably more serious; let’s not say whether you get physical access to your computer, in that case, it does not matter how you protect yourself.
Therefore, this is not an excessively serious case; Although it will undoubtedly be tested by hackers and attackers in some situations, if the AMD patches arrive on time it should not be a problem.
So, what do you think about this? Simply share all youw thoughts and opinions in the comment section below.