We all know very well that on more than one occasion we have talked about the dangers of installing applications manually when we do not know their origin. However, recently, a security firm has discovered a flaw through which anyone can inject malware into Android apps without altering signatures.
Hackers Can Inject Malware Into Android Apps Without Altering Signatures
On more than one occasion we have talked about the dangers of installing applications manually when we do not know their origin. GuardSquare, a company dedicated to digital security, has released a report explaining a new vulnerability called Janus that allows infecting applications in a very subtle way.
When we update an application, Android verifies with a process comparing the previous signature with the new one. If it matches, the new version is installed. Janus avoids this step of security and makes it possible to incorporate malicious code without us noticing. However, we can stay quite calm simply because of its limited scope.
A failure with very short legs
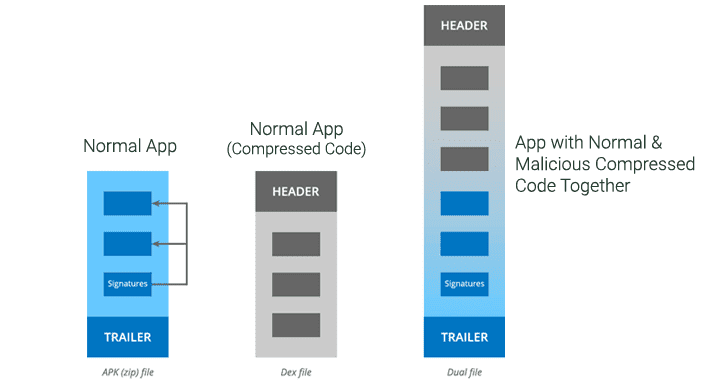
In Android, an application consists of an APK file, which we sometimes download simply to install an app manually, which is basically a compressed document with random bits at the beginning and later contains all the files and data of the application. On the other hand, we have a DEX file, which acts as a spindle and is independent of the verification of the signature so that you can modify and add content.
Hence, it can be installed without us noticing an application that is identical to the one we were using before updating it but with some malicious function that is not visible to the naked eye. This vulnerability was sent to Google by GuardSquare in the summer and revised in November, posting the notice in the December Android security bulletin.
Do we have to worry about this malware?
Not much, its scope is very limited and there have to be very specific circumstances for us to be infected. First of all: if we have a mobile with Android 7.0 Nougat and only download apps from Google Play, we do not have to worry about it in the least.
For a long time, the tech giant Google has used signature scheme v2 that prevents Janus from working, so any Android that downloads apps from the Google Play app store or has a moderately updated mobile can continue to use the apps as they have up until now. Although we have known about this ruling right now, we can see that there is little to worry about.
If we have a mobile with Marshmallow and we use old applications that use signature scheme v1 to verify the signatures. We are talking about apps that have not been updated for a long time or have been abandoned by their creators. If you suspect that you have an app of this style, be careful but it is very unlikely that it will touch you.
What happens with pages where we can download APKs like APK Mirror?
What to check if they have taken measures to patch this vulnerability. In the concrete case of APK Mirror, they have reviewed all the content exhaustively and Artem, its founder, assures that everything is in order and originally they did not have any application with signature scheme v1.
So, what do you think about this vulnerability? Simply share all your views and thoughts in the comment section below.