Millions of LinkedIn users are getting email services with guidance for immediate password change. What’s the reason? A data leak that would have happened in July 2012 may have affected 167 million accounts.
LinkedIn acknowledges that in 2012, its servers were hacked, resulting in the leakage of passwords.
More Than 160 Million LinkedIn Data Are On Sale At Deep Web
At the time, the reaction was as expected; the accounts involved, an estimated 6.5 million, had to go through a password reset. In addition, the company issued notices to advise others to do the same as a precautionary measure.
This week, LinkedIn found that the problem did not end there: a member of a darknet called TheRealDeal put on sale a package to access data of 117 million LinkedIn accounts obtained in casting 2012. The price kept by the member of the darknet is 5 bitcoins (US $ 2.2 billion, approximately).
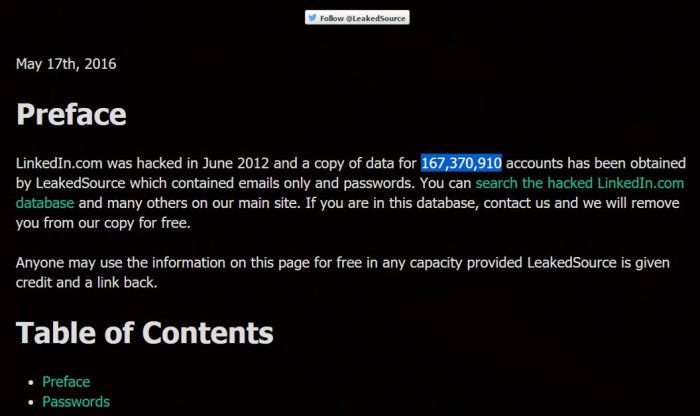
Several beads can be most affected. The LeakedSource is a site that describes itself as a service that helps the user find out if their private information is available on the Internet. It also claims to have access to the data of 167,370,910 accounts.
According to LinkedIn, no other major invasion was recorded in the service, so the data in these accounts have certainly been obtained even in the leakage of 2012.
If the number of accounts is so broad, why was only available data made available? One of those responsible for LeakedSource explained to the motherboard that “Probably the data was all the time under the control of a small Russian group.
Access to the package may have been well controlled to avoid fanfare, which would make many passwords be changed quickly”.
Also added, “from what you know, passwords themselves were encrypted, but without the application of “salt” (salt), key derivation technique that helps in the protection of combination of certain types of attacks. Because of this, people with knowledge on the subject do not have difficulty identifying passwords”.
Hence, LinkedIn had no choice: from Wednesday 18, service users will receive an email to exchange passwords. The reinforcement service is progressively invalidating passwords for all accounts created by 2012. The same has been done for the accounts which have not been updated since that year.
As expected, LinkedIn has been questioned by experts in security for failing to take measures more comprehensively compared to 2012.
For the invasion, Brad Taylor, the Proficio security company’s CEO, analyzed and performed forensics that could have given a clearer idea of the scope of the problem. The company defends itself by saying that it “strengthened the encryption of passwords and implemented the authentication option in two steps”.
But as the damage is done, it will do everything possible to protect. But the trick is to change your password on LinkedIn as soon as possible, even if your account has not been notified.