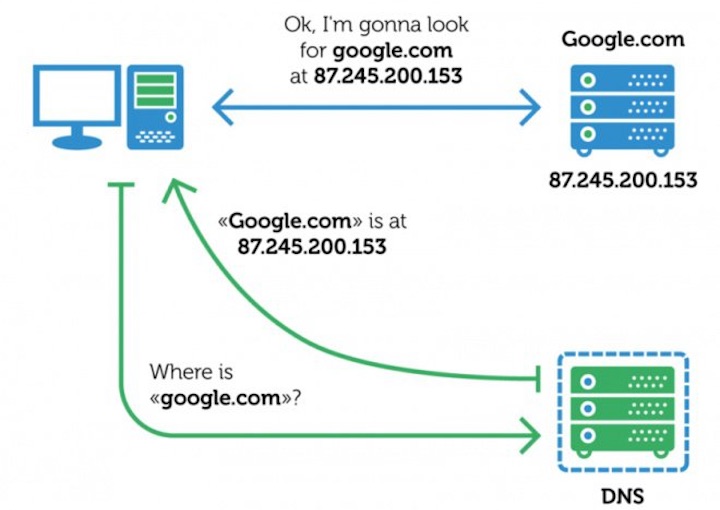
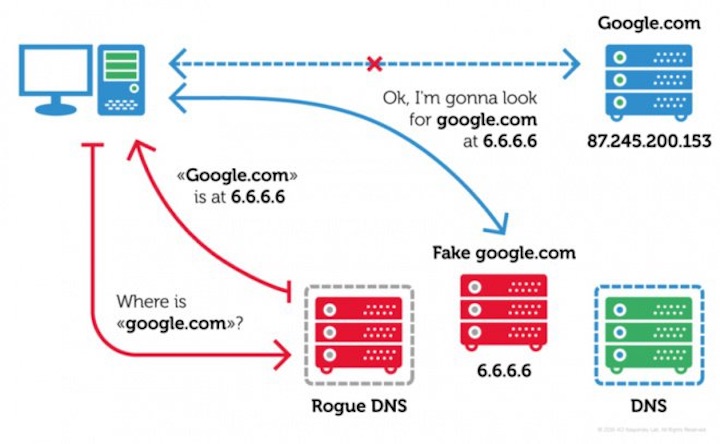
Recently a new malware has been discovered which instead of stealing the user data it simply prefers to attack the routers that the user connects to by changing the DNS.
This Android Malware Hijacks Router DNS From Smartphone
Security holes in Android are no longer a novelty and have become something that is almost “normal.” This is not a perfect system, it is the most used and this allows greater exposure to security problems.
New malware has been discovered, and instead of stealing user data, it prefers to attack the routers that the user connects to by changing the DNS.
This new malware from Android, which is being called the Switcher, has an entirely different approach than it has seen until today. It does not focus on user data or on the operating system itself. It prefers to attack other elements of the network to which the smartphone is connected, preferring to target Internet access routers, where it tries to change the defined DNS servers.
By doing so, it gains greater control over the remaining equipment and ensures a much greater impact on everyone connecting to the infected network starts using these new DNS servers.
Does this attack work on Android?
As we said before, the Switcher does not look at Android and prefers to use it as a means to get to the routers that give access to the Internet, propagating in the wireless networks where Android connects. The idea of this malware is to change the DNS servers defined, starting to use another, controlled by the attacker.
To be able to access these routers, the Switcher uses a brute-force technique, trying to discover the access data, resorting to well-known dictionaries.
After accessing the routers, it can detect the equipment and change the defined DNS servers using javascript and web access. The brand of routers that the Switcher most seeks is the TP-Link.
When you achieve this change, you will have these servers defined on all the devices that connect to that network, since most of them receive these servers through the DHCP service.
The result will be to refer users to sites that have nothing to do with the ones they want to visit, where they will receive unwanted advertising and even new malware and virus infections.
As far as we know, this malware is being propagated through a fake search application in Baidu and another that is dedicated to sharing access to wireless networks.
This is one more reason to take extra care and do not leave your devices set up with factory passwords or passwords that are simple and easy to guess. So far there is still no solution to this problem.