After a storm in May provoked by WannaCry, the bonanza seems to reign. As recently, the security company FireEye has announced that hackers are now using WannaCry Exploit simply to snoop on hotel Wi-Fi for stealing the important data of its guests.
WARNING! Hackers Are Now Using WannaCry Exploit To Snoop On Hotel Wi-Fi
After a storm in May provoked by WannaCry, the bonanza seems to reign. However, its strands are those that begin, now to worry. It is known that this ransomware was born of the ‘EternalBlue’ exploit that was published by the ‘The Shadow Brokers’ group as part of the tools used by the NSA in espionage and global surveillance tasks.
Hotels are now the target of the Russians
Not only did EternalBlue bring WannaCry to life, but also to NotPetya and EternalRock, malware that uses even more NSA exploits and is more powerful than WannaCry. This week, the security company FireEye has announced that ‘EternalBlue’ is being used to attack hotels in Europe and through the Wi-Fi network, it is stealing the data of its guests.
‘GameFish’ from APT28 crackers
FireEye points out that behind this attack are hacking group APT28, also known as Fancy Bear, the same group that was named as responsible for the attacks in the United States presidential election. APT28 is a criminal group of crackers that is related to Russian military intelligence.
This new malware, called ‘GameFish’, takes advantage of a security vulnerability in the Windows Server Message Block (SMB) network protocol, which allows you to access the entire network relatively easily and without attention.
But how does the attack work?
This attack has some curious peculiarities. The attack begins with the traditional phishing campaign, which in this case was targeted at hotel chains, where up to now cases have been detected in seven European countries and one in the Middle East.
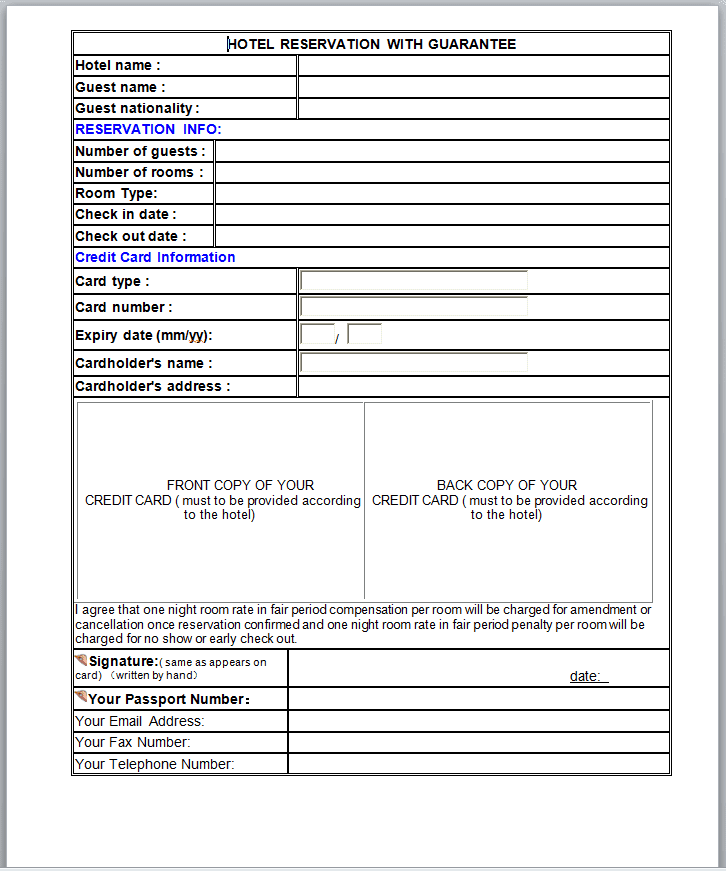
The e-mail arrives with a document with the “Hotel Reservation From.doc” attachment containing macros that perform a ‘GameFish’ installation on the machine and that spreads throughout the hotel’s local network. The malware clears the way and locates the computers responsible for controlling Wi-Fi networks and, after gaining control of the machines, it controls the traffic passing through this network, both the hotel’s administrative data and the data of the users who are traveling through the network.
Security experts believe that the purpose of this malware is to obtain information from government-related guests and important companies by using network control to extract the security credentials of anyone. The advantage (or disadvantage) is that you can only have access to those who do not have the two-step authentication method enabled, so that the user, when attacked, will receive an SMS or notification through an app (as is the case with Authentication from Google or Apple, for example) to confirm the access permission and there may stop the attack. This way your data will remain secure.
This attack coincides in some points with the “DarkHotel”, a similar malware that was propagated in some hotels last year, however, it was not yet spoken in ‘EternalBlue’. Security company FireEye mentions that despite these similarities both attacks are unrelated, as it was discovered that the malware “DarkHotel” only attacked Korean targets. On the other hand, while GameFish was designed to collect passwords, DarkHotel was focused on modifying software updates.
So far there is no simple way to stop the progress of GameFish from the moment this malware is already installed. Thus, the company recommends that free Wi-Fi networks must be avoided where possible and that even using these networks, they can not access sensitive and important content through them.
So, what do you think about this new exploit? Simply share your views and thoughts in the comment section below.