A new phishing campaign has been found by the researchers. The Armorblox research team discovered a Whatsapp Voice Message phishing attack.
This phishing attack spoofed voice message notifications on multiple customer tenants of Office 365 and Google Workspace.
Whatsapp voice message attack spread information-stealing malware to at least 27,655 email addresses.
Beware Of New Incoming Voice Message Phishing Scam
This phishing campaign aims to make the recipient install malware and steal the credentials. Stealing information through malware is increasing day by day via different means, but phishing attack comes first for hackers.
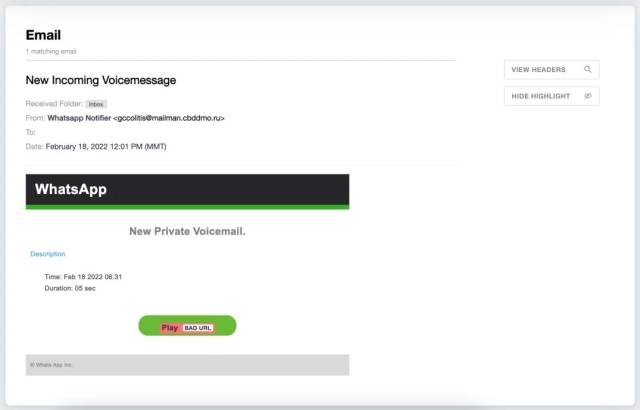
According to the Armorblox research team, the victims received malicious emails titled “New Incoming Voice Message” that shows the victim got a new private voicemail from Whatsapp.
The email asks the victim to click on the Play button to view the message. The researchers suggest that the email domain (mailman.cbddmo.ru) associated with the Center of Road Safety of the Moscow Region belongs to the Russian Ministry of Internal affairs page.
The victim received an email from a valid domain and bypassed the Microsoft and Google email security.
Armorblox said, “It’s possible that attackers exploited a deprecated or old version of this organization’s parent domain to send the malicious emails.”
When the user clicks on “play,” the recipients were taken to a page asking to install a trojan horse JS/Kryptik. When the victim opens the page, they are asked to confirm that no robots option. If you click on “allow,” the malware will steal sensitive information.
The email attacked the employee gamut of techniques to get past email security filters and pass the eye tests of victims.
The acctakers spoofed the popular messaging app and attempted to build trust by sending voicemail.
So, you need to beware as Whatsapp does not send any notification emails. If you get an email, we recommend you to avoid opening it to be safe.