We all know very well that the WordPress is arguably the free digital content platform most used worldwide. According to the recent data, 30% of all websites available on the internet use WordPress but the platform currently has a security flaw that allows users to delete files that are fundamental to the operation of sites that are based on this platform.
This WordPress Flaw Gives Attackers Full Control Over Your Site
The WordPress is arguably the free digital content platform most used worldwide. According to the recent data, 30% of all websites available on the internet use WordPress but the platform currently has a security flaw that allows users to delete files that are fundamental to the operation of sites that are based on this platform.
If you have a site based on this platform, then know what can happen and how to fix it.
WordPress is undoubtedly one of the most popular content management platforms. With this platform, the user can easily create websites, blogs, e-commerce sites, etc in a fast, simple and very professional way.
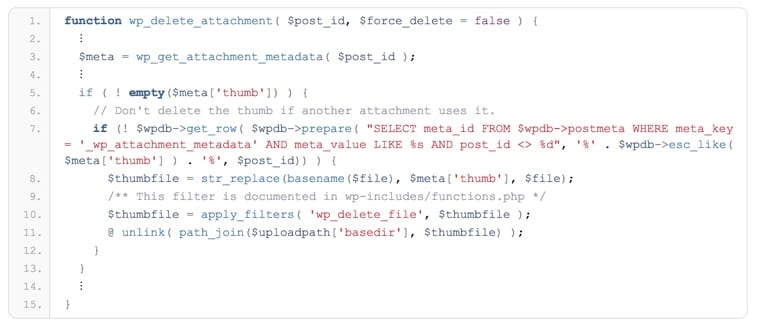
However, according to the researchers at RIPS Technologies GmbH, this platform has a serious security flaw, identified in one of WordPress’s functions. This function is only executed (in the background) when a certain user tries to permanently delete the thumbnail of an image from the back-office. Through this function, important WordPress framework files such as .htaccess, index.php or wp-config.php can be deleted.
This bug is available to all types of WordPress users. For example, a low profile author user can delete files from the structure without having higher privilege levels.
Also, note that the researchers reported the failure about 7 months ago and nothing was done. It is also known that this bug affects all versions of this platform, including version 4.9.6. The researchers provide here a way to temporarily fix such vulnerability.
So, what do you think about this? Simply share all your views and thoughts in the comment section below.