If you have been using the Windows operating system for a while, you might be familiar with the CMD or Command Prompt. Command Prompt is a command-line interpreter often considered the most powerful tool in Windows. You can run CMD with administrative privileges to access the core features of Windows.
Command Prompt is helpful, but hackers often use it for the wrong purpose. Security experts also use the command prompt to find potential security loopholes. So, if you are willing to become a hacker or security expert, this post might help you.
Also Read: How To Remove Computer Viruses Using CMD
10 Best CMD Commands Used In Hacking
This article will share some of the best CMD commands used for hacking. So, let’s check out the list of best CMD commands for Windows 10 computers.
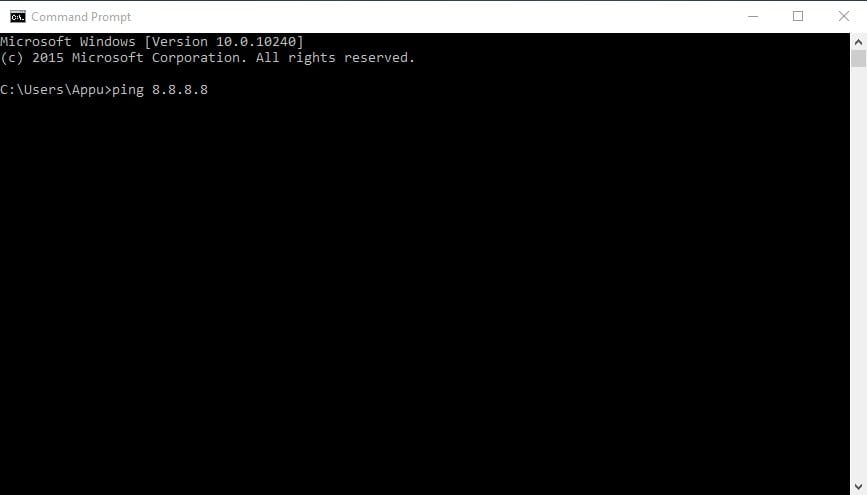
1. ping
This command uses your internet connection to send some packets of data to a specific web address then these packets are sent back to your PC. The test shows the time it took to reach the particular address. Simply put, it helps you know if the host you are pinging is alive.
You can use the Ping command to verify that the host computer can connect to the TCP/IP network and its resources.
For example, you can type in the command prompt ping 8.8.8.8, which belongs to Google.
You can replace “8.8.8.8” with “www.google.com” or something else you want to ping.
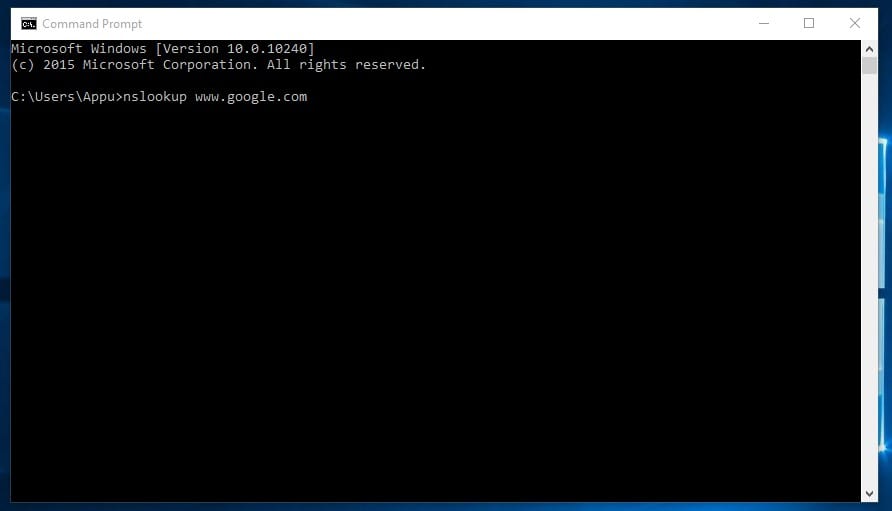
2. nslookup
It is a network administration command-line tool that helps you obtain a domain name or IP address mapping for any specific DNS record. The nslookup is often used for obtaining the server records.
Suppose you have a website URL but want to know its IP Address. You can type in CMD nslookup www.google.com (Replace Google.com with the website URL of which you want to find the IP address)
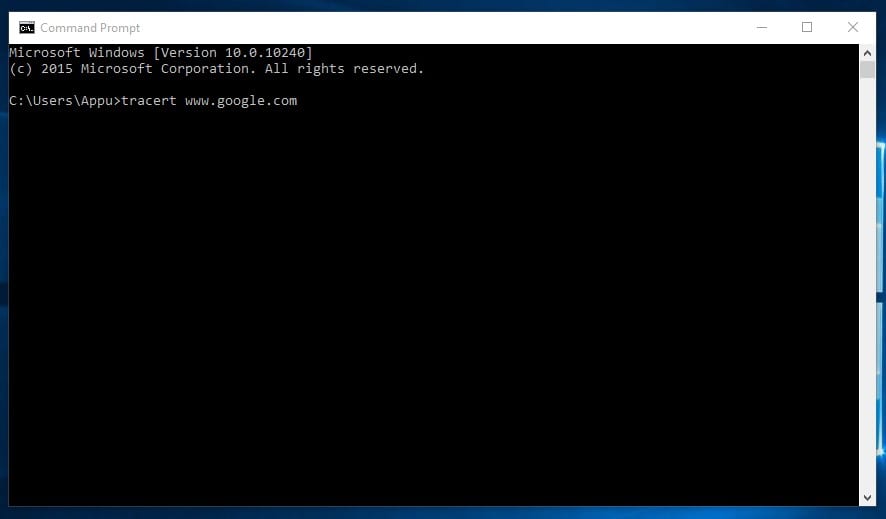
3. tracert
You can say Trace Route. Like its name, it allows users to trace an IP’s route to reach a destination. The command calculates and displays the time each hop took to reach a destination. You need to type
tracert x.x.x.x (if you know the IP Address) or else you can type tracert www.google.com (If you don’t see the IP address)
4. arp
This command helps you to modify the ARP cache. You can run an arp-a command on each computer to see whether the computers have the correct MAC address listed to ping each other to succeed on the same subnet.
This command also helps users find out if anyone has done arp poisoning in their LAN.
You can try typing arp-a in the command prompt.
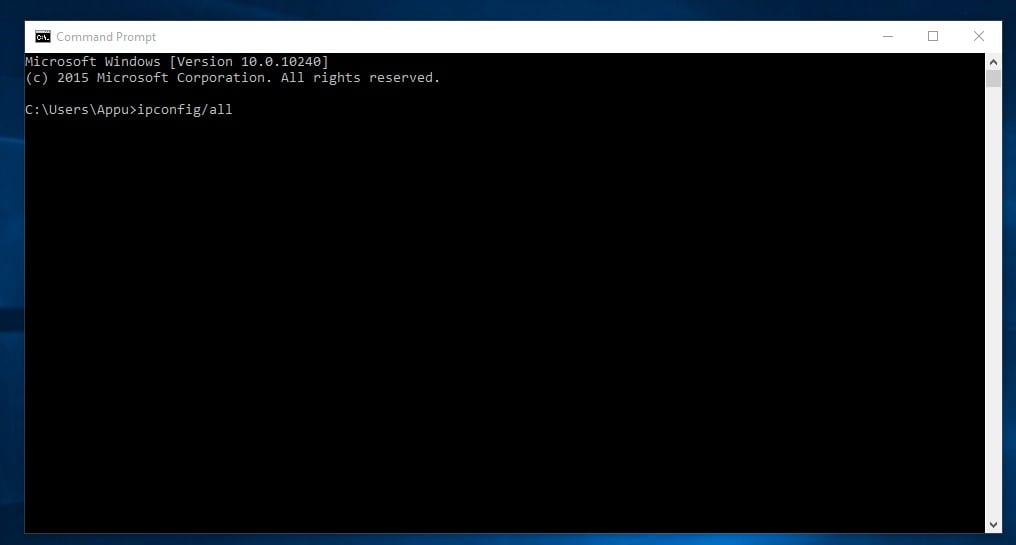
5. ipconfig
This is the command which shows every helpful thing. It will show you the IPv6 address, temporary IPv6 address, IPv4 address, Subnet Mask, Default gateway, and all other things you want to know about your network settings.
You can type in the command prompt “ipconfig” or "ipconfig/all"
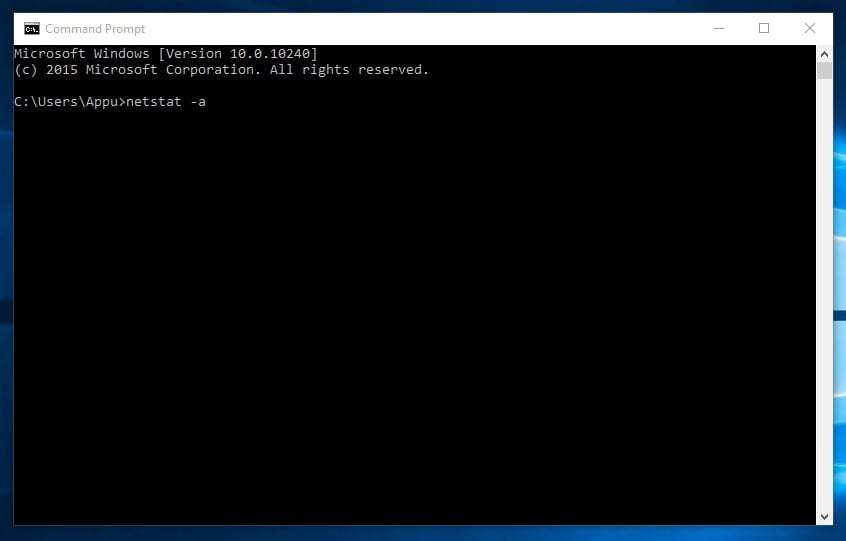
6. netstat
If you want to find out who is establishing a connection with your computer, you might try typing in the command prompt “netstat -a”. It will display all the contacts and learn about the active links and listening ports.
Type in command prompt "netstat -a"
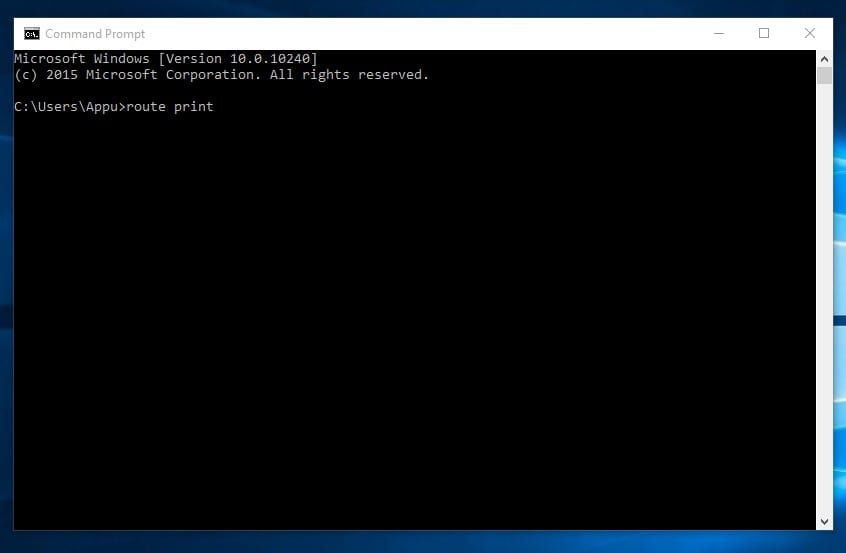
7. Route
It is a command to view and manipulate the IP routing table in the Microsoft Windows operating system. This command will show you the routing table, metric, and interface.
Hackers often use the Route command to distinguish between routes to hosts and routes to network. You can type in the command prompt "route print"
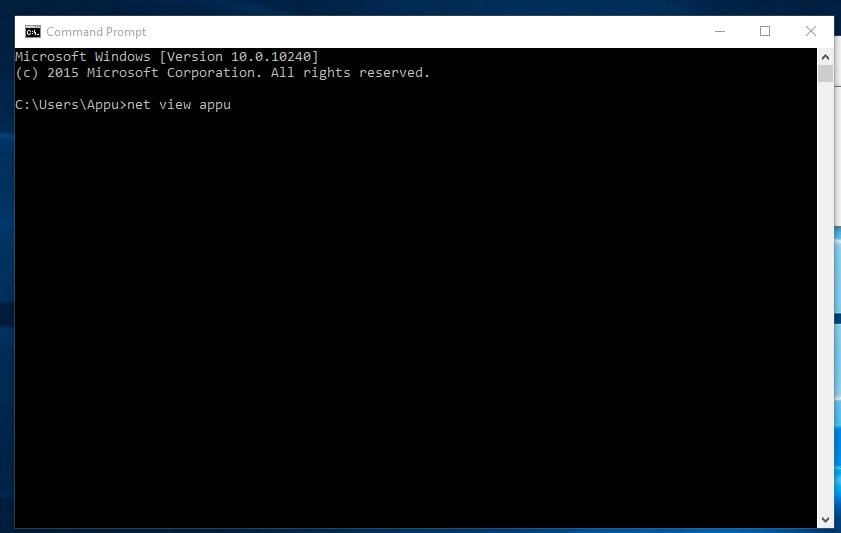
8. Net View
This command displays the list of resources, computers, or domains shared by the specified computer.
On Windows, you can use the Net View command to find computers in your network whose network discovery is turned on.
You can type in the command prompt "net view x.x.x.x or computername"
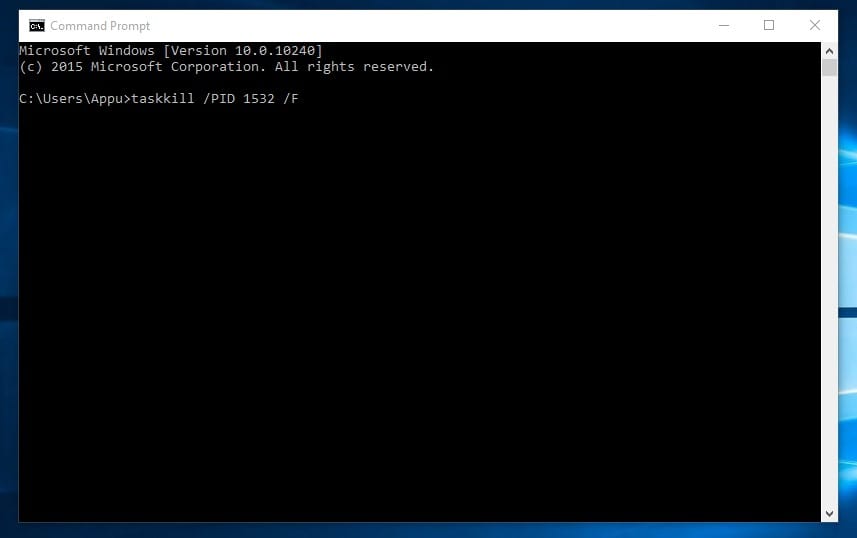
9. Tasklist
This command opens up an entire task manager on the command prompt. Users need to enter the tasklist on CMD, and they will see the list of all running processes. You can figure out all the wrongs with these commands.
Moreover, you can also use the command to close any process forcefully. For example, if you want to kill PID 1532 process, then you can enter the command:
taskkill /PID 1532 /F
10. Pathping
The pathping command is similar to the tracert but shows more detailed information.
The commands take a few moments to complete as it analyzes the route taken and computes packet loss. On the Windows command prompt, type in the following command
pathping techviral.net (Replace techviral.net with the one that you want to ping)
You can explore more than this; we have listed the Best CMD commands in one of our articles! I hope you like the post! Please share it with your friends too. Leave a comment below if you want to add any command to the list.
Hi, when I typed the netstat command a very long list appeared of devices supposedly listening and others had things like ”established” and ”Time_Wait” and ”Close_wait” could you tell me what this means? i don’t know much about this stuff so right now I’m freaking out thinking people are listening to me or something. Everytime i turn on my computer windows powershell is opened and idk why because i don’t have it scheduled or anything. Could you explain why? Thank you.
no. we can’t explain why… I wrote a long response and the mods deleted it, lol. apparently they don’t want you to know.
Sorry sir, now you can explain 😀
shutdown