Beware! Hackers Are Spreading Locky Ransomware Using Facebook Messenger. Don’t click any .svg image file delivered to your Facebook messenger.
Hackers Are Spreading Malicious Images On Facebook
Spammers are using Facebook’s instant messaging (IM) feature to spread a critical malware. So, Don’t click any .svg image file delivered to your Facebook messenger because it might lock your entire system completely.
Hackers have targeted Facebook messenger to spread Locky Malware. Locky malware has now one of the favorite ransomware tools for spammers and it normally spreads via Spam emails with a hidden downloader.
Malware researcher, Bart Blaze was the first one to spot the attack. The malware even has the potential to bypass Facebook’s file extension filter. Hackers are using .SVG image extension to spread a malware downloader called Nemucod. Therefore, if you have received anything similar then don’t click it.
Now you might be thinking why hackers considered SVG (Scalable Vector Graphics) file for spreading the ransomware. Well, Javascript can be embedded in SVG extension so that it can open in a web browser. Hackers have embedded the Javascript code inside the image which was actually a link to an external file.
If anyone clicks the file then it will redirect you to a website mimicking YouTube, but with completely different URL. Then you will be asked to install a Chrome extension to view the video.
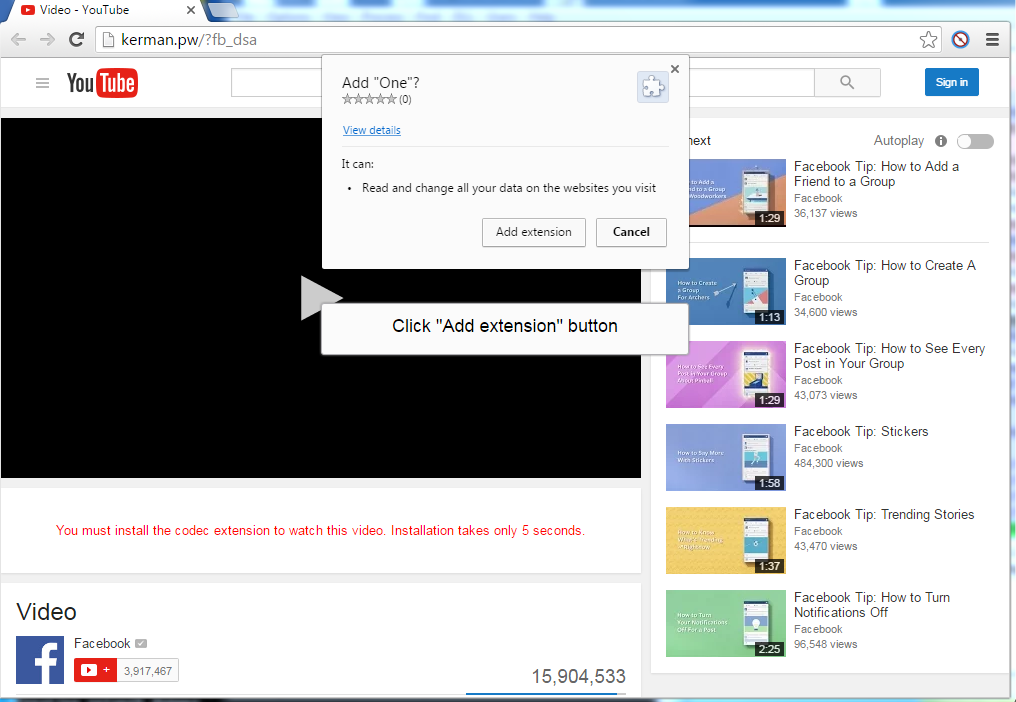
Once you install the extension, Hackers can alter your data regarding websites they visit and can even have full access to your Facebook account to securely deliver the SVG image file to all your friends.
Peter Kruse, another Malware researcher had also shared some darker part of the story. He said that image files containing the Nemucod Downloader had the ability to download a copy of Locky ransomware on victim’s PC. The attacker can lock down sensitive files from the victim’s PC and can demand a financial fee for their return.
Confirmed! #Locky spreading on #Facebook through #Nemucod camouflaged as .svg file. Bypasses FB file whitelist. https://t.co/WYRE6BlXIF pic.twitter.com/jgKs29zcaG
— peterkruse (@peterkruse) November 20, 2016
If you think that you had accidentally clicked on anything suspicious then you need to head over “Extension manager” on google chrome and look for any extension that looks suspicious, Usually, this type of extension doesn’t have any icon. You can search for the following descriptions in the extension manager
“One ecavu futolaz corabination timefu episu voloda
Ubo oziha jisuyes oyemedu kira nego mosetiv zuhum”
If you find any of the extension that matches the above description then simply clicking on the Remove button will delete it. Users can then change his/her password and can perform a full antivirus scan.
So, what you think about this? Share your thoughts in a comment box below.