We all know very well that all the unhandled security holes end up in malicious hands and are exploited for their own benefit in the form of malware or viruses. Spectre and Meltdown are the latest flaws available and the first attacks that start to exploit them are starting to emerge.
Meltdown/Spectre-Based Malware Coming Soon To Devices Near You
All unhandled security holes end up in malicious hands and are exploited for their own benefit in the form of malware or viruses. Spectre and Meltdown are the latest flaws available and the first attacks that start to exploit them are starting to emerge.
There is not much information yet on these new forms of attack, but the AV-TEST security application testing company has revealed that forms of attacks, mostly malware, have already begun to exploit the Meltdown and Spectre flaws in almost all modern processors.
Initially revealed to affect Intel processors, these two failures have proven to be in many other manufacturers and architectures.
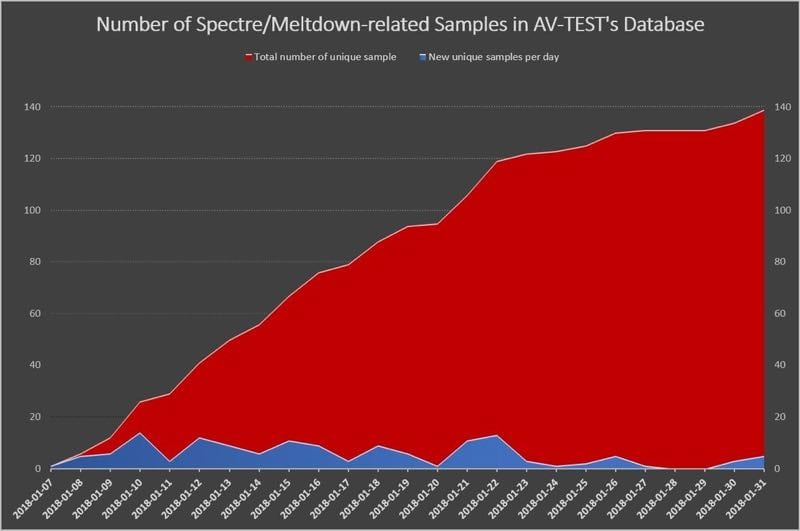
According to AV-TEST, there are already 139 samples that have been collected and are appear to be trying to exploit these two vulnerabilities and then gain access to user information.
From the information gathered, this malware comes in the form of binaries, that is, applications that can be executed, existing in the Windows operating systems, macOS and Linux. There is also javascript code, which seeks to exploit Spectre’s vulnerabilities, but via the browser.
Most samples are binaries (compiled for Windows, Linux and MacOS), but we also found the first working JavaScript PoC for Spectre. The latest (just-released) versions of e.g. Chrome and Firefox includes special fixes, so at least the PoC won't work anymore.
— AV-TEST GmbH (@avtestorg) February 2, 2019
It is important to note that this is an even more serious threat, as there are still many machines and systems that are not protected by a process of updates that many consider having been disastrous. Most browsers will already be protected in the latest versions.
If your systems have not yet been updated, this is the right time to do so. The attackers have access to the code that proves the flaws, converting these flaws into malware that can then be used for a variety of criminal purposes.
So, what do you think about this vulnerabilities and flaws? Simply share all your views and thoughts in the comment section below.