According to a report, Borat named a new remote access trojan (RAT) that appeared on darknet markets, which offers easy-to-use features to conduct UAC bypass, DDoS attacks, and ransomware deployment.
Cyberattacks have increased a lot nowadays, even on high prestige tech companies. Recently a hacking group named Lapsus$ has breached data from companies like Samsung, Nvidia, Ubisoft, and Microsoft.
The RAT’s developers decided to name it after the main character of the comedy movie series Borat, which featured the popular Sacha Baron Cohen as the protagonist. Still, this malware is no joke at all.
New Borat Malware Doesn’t Mean Any Joke
Currently, It’s unclear if the Borat RAT is sold or freely shared among cybercriminals. Still, Cycle says it comes in the form of a package that includes a builder, the malware’s modules, and a server certificate.
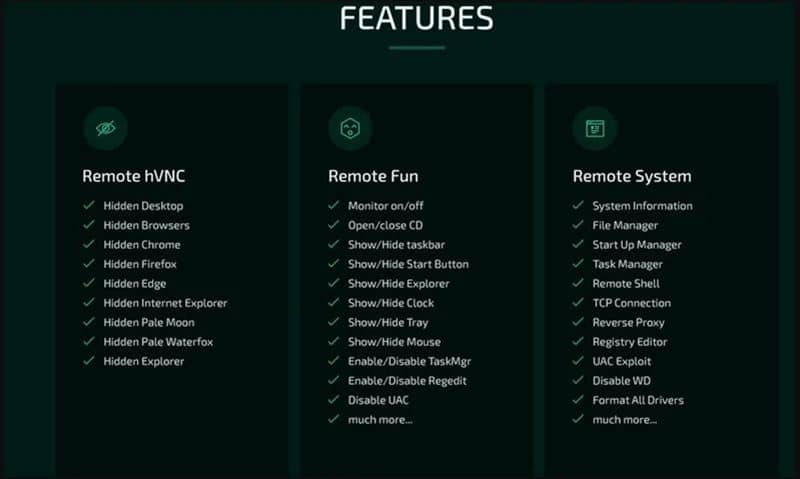
Some prominent features of the trojan, according to Cyble, include the following:
- Ransomware – deploy ransomware payloads onto the victim’s machine and automatically generate a ransom note through Borat.
- DDoS – direct garbage traffic to a target server by using the compromised machine’s resources.
- Remote desktop – start a hidden remote desktop to perform file operations, use input devices, execute code, launch apps, etc.
- Reverse proxy – set up a reverse proxy to protect the remote operator from having their identity exposed.
- Device info – gather basic system information.
- Process hollowing – inject malware code into legitimate processes to evade detection.
- Credential stealing – steal account credentials stored in Chromium-based web browsers.
Some other minor contains hiding the desktop, hiding the taskbar, holding the mouse, turning off the monitor, showing a blank screen, or hanging the system.
According to Bleeping Computer, the above features make Borat a RAT, spyware, and ransomware, so it’s a powerful threat that could conduct harmful activities on a device.
Specifically, the threat actor is distributing these tools as cracks for games and applications, so be careful not to download anything from untrustworthy sources such as torrents or deceptive sites.
Disclaimer: TechViral doesn’t support any malware or any cyber activity. TechViral is mainly against these types of activities; all above content is only for information or as preventive.