Cyber Criminals are misusing two noted exploits to install a ransomware on Android devices with older versions. This happens when the Android users access websites that load malicious Ads.
New Malware Can Infect The Android Device By Just Visiting A Website
In Windows, we have seen that web based attacks occur when the user installs a malware hit plugins, however it is not common in Android, where the application security model is secure.
However, researchers from Blue Coat Systems discovered a new malware that can attack an Android device without any user interaction. Normally, malware in Android requires user to install specific APK file, but when a user visits malware hit website, his/her device gets infected. The researcher recently tested Samsung tablet running on CyanogenMod 10.1, which is the open source version of Android 4.2.2, it was infected after visiting a website that showed a malicious ad.
“This is the first time, to my knowledge, an exploit kit has been able to successfully install malicious apps on a mobile device without any user interaction on the part of the victim,” stated Andrew Brandt at Blue Coat.
“During the attack, the device did not display the normal ‘application permissions’ dialog box that typically precedes installation of an Android application.”
Researchers also disclosed that ad contained JavaScript code that exploited vulnerability in libxslt. The libxslt exploit was among the files leaked last year from surveillance software maker Hacking Team.
The explotit uses ELF executable dubbed as model.so on the device that inturn exploits another vulnerability to acquire root access, which is considered as highest privilege on the device. The root exploit used by module.so is called Towelroot.
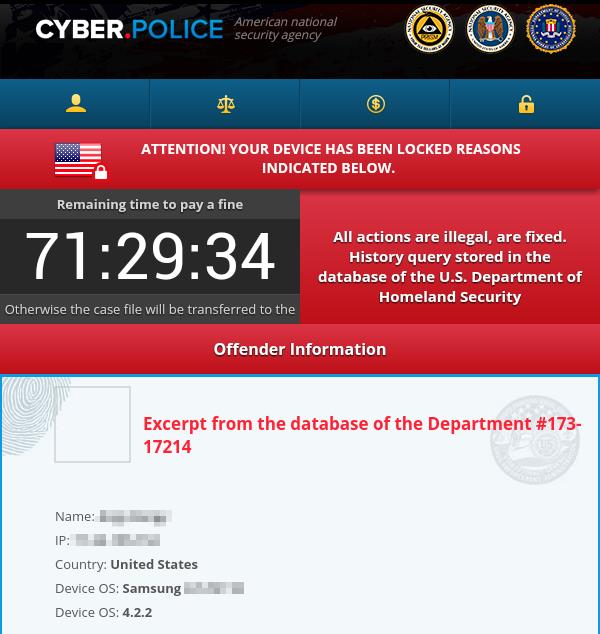
After the device is infected, Towelroot downloads and installs ransomware file via APK which is called Dogspectus or Cyber.Police.
In most mobile ransomware programs, we have seen that they encrypt user files, however this ransomware does not encrypt files. It displays a warning which is a hoax, it claims that that this message is from law enforcement agencies and invalid activity was detected on the device, so the user has to pay a fine.
The malicious application prevents users from doing any activity on the device till the user pays a fine. The second option erases all files from the device, so it is recommended to connect the device to a computer and save your files.
The researchers also found a method to get rid of this. The users affected will need to do a factory reset, which will delete applications installed. Remember, by doing factory reset, you should have a backup of your data. Also, keep in mind not backup your files on the device’s memory, instead save your backup in your computer.