Just after wrecking destruction on unpatched Windows systems using WannaCry Ransomware, now few notorious hackers from the China are targeting Android devices.
Beware! A New WannaCry-Inspired Ransomware Is Attacking Android Smartphones
Since Ransomware appeared WannaCry, which was able to take advantage of two different exploits (Double Pulsar of the group ShadowBrokers and EternalBlue of the NSA) and affected thousands of machines with Windows, this has served as inspiration for many other attacks.
Recently WannaLocker was discovered, a ransomware for Android inspired by WannaCry.
Digital security must now be regarded as something very serious, for our good. After the WannaCry attack, which especially targeted the victims’ machines that were not upgraded. WannaLocker was now discovered, a ransomware targeted at Google’s mobile operating system, Android.
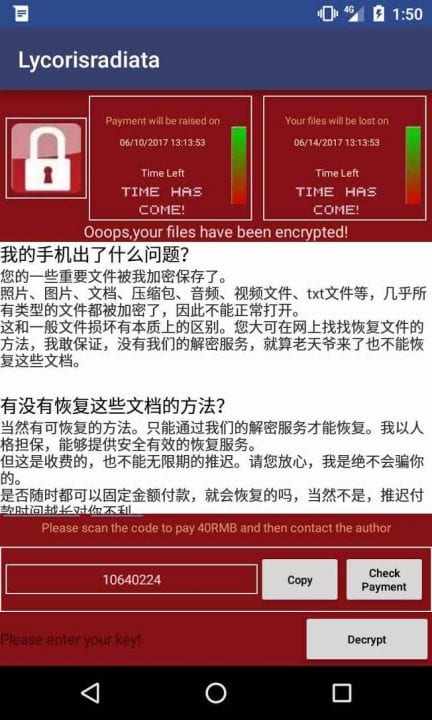
According to the information, this ransomware was created by the Chinese hackers and, contrary to what happens with other ransomware types, where the payment is made through BitCoins the WannaLocker requires a payment of 40 Renminbi (about $ 6) through various Payment services, such as QQ, Alipay or WeChat.
This ransomware uses AES to encrypt information and adds a Chinese character set at the end of each file name.
According to Nikolaos Chrysaidos of Avast, this ransomware only encrypts information that is in the external memory of the equipment. Because features are limited on Android devices, ransomware only encrypts files under 10KB, excluding those found in the “Android”, “with”, “DCIM”, “download” or “miad” directories.
As always, pay attention to what you install on your system and what permissions are requested. The information we have is that this ransomware arrives through games that are available in Chinese forums.
So, what do you think about this? Simply share your views and thoughts in the comment section below.