Here we have listed 10 Important Steps to Take After Data Breach, whose implementation is a must if you face such a condition as it will help secure further attacks and help find the attacker.
Because of the data breach, multiple companies get hacked in a year. Ask for their privacy to the information is leaked, and hence their base gets damaged in the market. For those new to the data breach words, we must tell you that this is the kind of data transparency that the hacker can attain. Due to this issue, they can pierce through the security walls and leak the impact of private information.
This happens to individual users, too and companies are not alone in bearing this threat. Now that you know about the data breach, what symptoms could you know about its existence in your network? What are the things you could do to prevent it or to stop it? These would be the questions arising in your mind, but being a beginner to this thing, you would be confused about that! For your insurance, we have written about every aspect of controlling and protecting data breaches in this article. Just go and read this article to know about that.
Also Read: Best Security Implementations To Do On MAC
10 Critical Steps To Take After Data Breach Attack
The method is quite simple and easy, and you need to follow the simple step-by-step guide we discussed below.
1. Isolate Your Network for some time
The best way to stop hackers from accessing your sensitive information is to isolate your network for some time. It’s hard to stop the system for some time. However, there are times when you need to take some major steps, and a major breach is one of the foremost reasons.
2. Check the Damage Cause
The first thing you need to check on your system or network is the amount of damage caused due to the data breach. Check if only some data have been a list or if your heavy data loss has occurred. This is important because, for the least loss, you don’t need to go through each and every step, but for the extensive loss, you would require doing so. Also, this helps to notify you about the effectiveness of an attack.
3. Change Credentials
If you notice any account whose information or data has gone leaked, quickly try to change the password for that account if you are attaining possession over it till the time. If you would take more time to this process, the hackers could get more time to breach through more of your data. This could also be dangerous as the hackers could avail the other malachite contents inside your account. Push back the attack and grasp your possession again.
4. Bank Details
If you have hacked the back details with the credit card or debit card details, then please follow up with your back contacts and furiously ask them to block your account transactions. Further, if the damage has already occurred, you should ask them for an inquiry. Your bank details are so important, and we believe that you would find it the very first thing to look after in case you get your data breached.
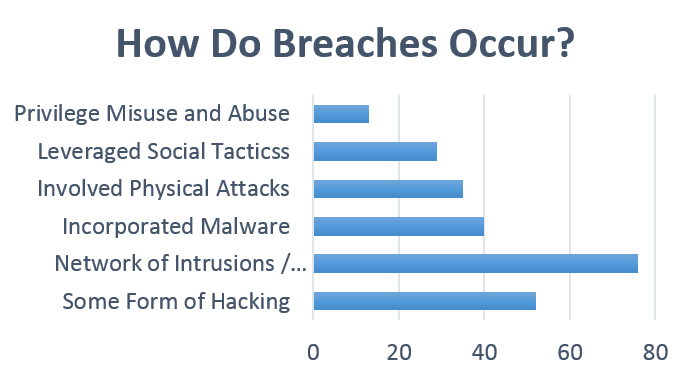
5. Find out How the breach occur?
It doesn’t matter how strong your IT Security is and how many barriers or security methods you impose on your people. As seen in the IT section, the weakest links in the system will always be your own employees.
Ask your teammates if they have mistakenly installed or downloaded a malicious installer on the system that gives access to hackers.
6. Check your Backups
Well, the IT department always has some backups for its main servers that ensure a faster recovery process in an emergency. Those logs can be used for recovery. Moreover, those logs can give you a clear look to compare changes before and after the breach.
7. Contract police and Cyber Crime Controlling Authorities
These authorities should be consulted by the insurance company if you find your credit details hacked or get your money stolen. This is important because the money stole-related cases could affect your credential bank status. These authorities work legally to find the offender and punish him for the attacks. Although you might not be able to get your lost money back, if that happens, your future protection will be safeguarded!
8. Report to the IRS in case of Identity Details Breach
It doesn’t matter I’d you contacted the police after your account details or identity details for hacked. This still makes the juggling spark of your identity is utilized negatively by the hackers. This happens often and is widespread so try to protect yourself from it.
9. Practice Analysing your Accounts
Yet make a habit of analyzing your bank accounts or any other credit accounts often regularly in the month. Ask for the full reports from the authorities regarding the transactions in your account. This is a killer way to make full surveillance of your account and hence judge for any interpretations or damages far before!
Also Read: Turn Your Android Device Into A Security Camera
10. Learn from the security breach
Learning from the security breach will help you prepare next time. Hackers are everywhere and will try to use their skills for evil things. Therefore, be prepared for the next time.
As nobody could be sure about the safety of the network as the hackers kept on finding new ways to pierce through the security walls. Although the hackers could not find ways to judge your steps for prevention. Just try to boost your security charges so that the hackers would not get the chance to come inside type private network world. Talking about the data breach, this may happen to anyone in this world, and I’d anyone is a victim of this revelry, then please follow the above steps fast to prevent your important stuff on your network! Leave a comment below if you have any related queries about this.