We all know that the creators of viruses and malware are increasingly becoming cunning and more creative. As they always try to find new ways to infect users and control their machines, but, now again they found another new way to do so.
This Fileless Malware Uses DNS Queries To Carry Out PowerShell Commands
The creators of viruses and malware are increasingly becoming cunning and more creative. They always try to find new ways to infect users and control their machines.
DNSMessenger is the latest form of malware to be discovered, with the particularity of being controlled exclusively by queries to the DNS service.
DNS is one of the essential services to the Internet and its use. It converts IP addresses into names and allows as soon as we can navigate just by typing the addresses of the pages we want to visit. But DNS has evolved over the years, and today it does much more than these conversions.
It is precisely through these additional functions, in particular in the TXT registers, that DNSMessenger works. This malware comes to computers in the form of a Word file, which actually runs a set of scripts in PowerShell.
After evaluating the system where it is and the permissions it has, DNSMessenger starts communicating with its control, always through DNS query, where it receives the commands through the obtained answers.
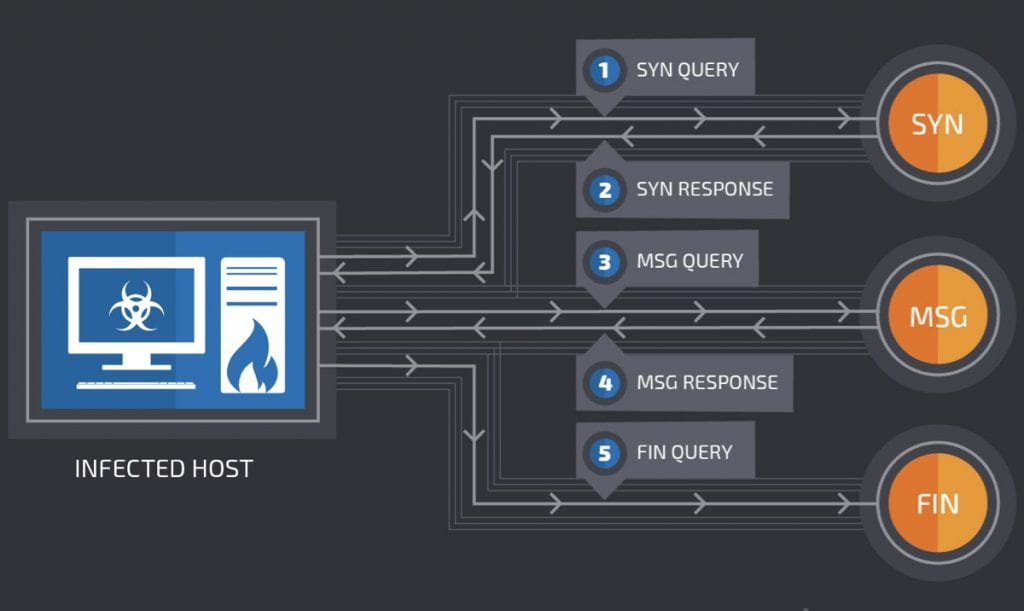
Why the use of DNS in DNSMessenger?
Using DNS to control malware has obvious advantages for attackers. The largest of these is the lack of records of these operations on computers, which makes it difficult to detect it as malware.
On the other hand, most defenses focus on the traffic analysis of much more used protocols, such as HTTP and HTTPS, which leaves DNSMessenger outside the evaluation radius of the protection systems and the traffic filters that by norm are applied.
This is further evidence that malware writers are increasingly becoming more sophisticated and are looking for new ways to go unnoticed while being more effective in their attacks.