Google’s 2016 year in review reports puts the spotlight on the bug bounty programs which shows that hackers were rewarded $3 million throughout 2016. More than 350 researchers from all over the world have contributed to Google’s bug bounty program and managed to report 1,000 bugs in Google apps and services.
Google Paid Hackers $3 Million In 2016 Bug Bounty Program
If you think that hackers always make money by engaging in criminal activity, then you were wrong! Giant companies now have bug bounty programs in which researchers were rewarded for disclosing existing flaws in the system.
Recently, Google’s 2016 year in review reports puts the spotlight on the bug bounty programs. Google has released the previous year results which show that hackers were rewarded $3 million throughout 2016.
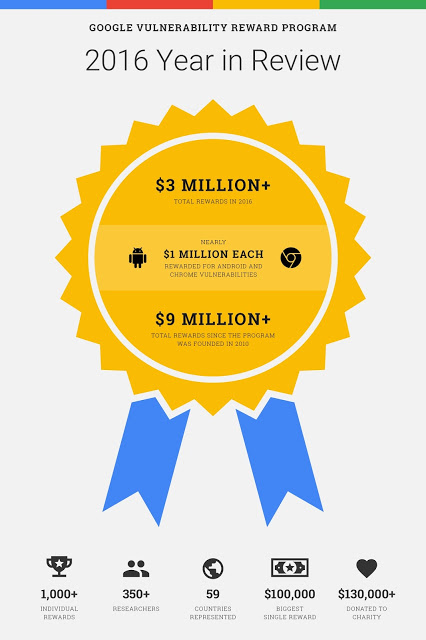
Google paid $2 million for the bug bounty program in the year 2015. Google had increased the minimum payout in 2016, in some areas even by a 50%. That’s why $3 Million represent a pretty significant hike.
In the year 2016, more than 350 researchers from all over the world have contributed to Google’s bug bounty program and managed to report 1,000 bugs in Google apps and services. You will be shocked to know that the highest payout for a single vulnerability report was $100,000.
Google has paid more than $9 million in total rewards since the program was founded way back in 2010. Eduardo Vela Nava, VRP Technical Lead, Google wrote:
“We saw amazing contributions from Android researchers all over the world, less than a year after Android launched its VRP. We also expanded our overall VRP to include more products, including OnHub and Nest devices. The vulnerabilities responsibly disclosed at these events enabled us to quickly provide fixes to the ecosystem and keep customers safe,”
So, what do you think about this? Share your views in the comment box below.