Let’s look at some of the Common Social Engineering Attack Tactics and How to Prevent Them. So that next time, you must be alert to such Kinds of attacks to secure your privacy.
Social networks and services around the internet are insanely popular among people. Almost every person globally has at least a single social media account. These highly intensified interests of the users on social media are focused on by some troops generally having harmful intentions; these people are commonly known as hackers. The motive of the hackers is to distract people and gain access to their essential digital information by breaking the network securities or making fools of them. There are pretty common two types of techniques that hackers use reputedly and, most of the time, gain success.
More often, people on social media never care about the hacking, and subtly, they get easily trapped for this reason. Their major techniques involve social networks and related services. This is to make people aware of such practices so they won’t get stuck in them. Here in this article, we have written about all the tactics and techniques used by hackers on social networks to hack information.
Also Read: Best WhatsApp Tricks and WhatsApp Hacks
Common Social Engineering Attack Tactics and How to Prevent Them
Below we have listed some of the attacks you should know about so that you can easily detect them in the future to get secure in this virtual world. So have a look at these attacks below.
Also Read: Best Hacking Tricks & Tips For Android
1) Phishing Attacks
These genuine-looking links sent to you through emails, messages, etc., take you to the login page. It then asks for your account credentials which, if you fill, will be shared with the connected hackers with the link. This sort of hacking method is simple to be justified and detected as it ends with asking for the account login and returns with the error process
2) Watering Hole Attack
This technique is similar to the Phishing technique, but now the source for trapping visitors is trustworthy websites. The hacker induced malware inside the actual websites that numerous people visit. The hacker gets the details of the visitors when they click on the poisoned links and fill up the credential fields. The rest of you know it happens like phishing only. To protect from water hole attacks, the toy must have powerful anti-malware and antivirus installed on your device. Also, use strong protection in the web browsers!
3) Pretexting
Through this technique, the hackers plot a great story to become genuine in the sense of people. They adopt well-known authority credentials and fake them to the people they text or call. After that, they commonly tell a service with the offer and all that all for the essential details. Those who provide their information get trapped, while those who deny making a good way out.
4) Tailgating
Never trust any stranger soon, and give away your details to prevent these attacks! This is how the hat trappers use to get inside personal or restricted areas with vital information. The trappers trick the people with real spoken stories or words, gaining their trust. Once these strangers gain confidence, they will likely pierce into your essential information within a few days.
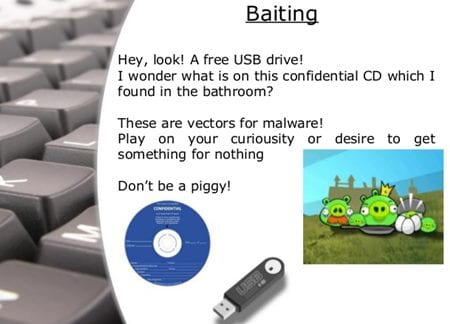
5) Baiting
They are providing free competitive, and paid stuff to the users and inducing the malware inside it before distribution. Be assured that you only download the apps, software pure tools through trusted websites! This technique is more often used, and people never find this attack.
Also Read: Best Tricks And Tips For Rooted Android
Please take the information given in this article seriously and always care about these hacking traps while using the technology or networks. Until there, the unit here is online, with few techniques hacking through social engineering, and no one can say about the future methods that could develop.
We hope you liked this article; please take some time to share this article and comment with your opinions too! We said this because we wanted to convey that even the protection of methods cannot fully ensure security! Yet you can ensure that you remain secure to the greatest extent.